
What is Ransomware?
Ransomware is malware that employs encryption to hold a victim’s information at ransom. A user or organization’s critical data is encrypted so that they cannot access files, databases, or applications. A ransom is then demanded to provide access. Ransomware is often designed to spread across a network and target database and file servers and can thus quickly paralyze an entire organization. It is a growing threat, generating billions of dollars in payments to cybercriminals and inflicting significant damage and expenses for businesses and governmental organizations.
How does Ransomware spread?
Users might encounter this threat through a variety of means. Ransomware can be downloaded onto systems when unwitting users visit malicious or compromised websites. It can also arrive as a payload that is either dropped or downloaded by other malware. Some ransomware are delivered as attachments from spammed email, downloaded from malicious pages through malvertisements, or dropped by exploit kits onto vulnerable systems.

How to identify ransomware strain (and its symptoms)
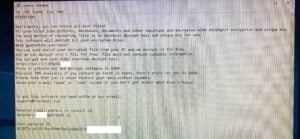
The most obvious sign of encrypted data is that the data has been converted to other formats (.locked .CRAB .KRAB .kodg .hets .mkos …) so they are inaccessible, slow/unresponsive computers, strange pop-ups/alerts, and the appearance of ransom demand messages (typically Readme.txt, or Recovery_My_File.txt).
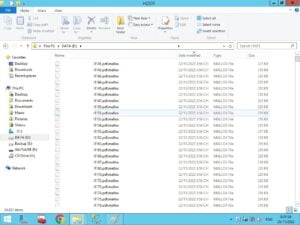
How to decrypt ransomware encrypted files?
Following a hacker’s demand to receive a decryption key is extremely risky and expensive. Many people and organizations have paid the ransom only to receive nothing in return. More dangerously, you could get repeated ransom demands.
There are several steps you can take to give you the best possible chance of minimizing damage and quickly returning to business as usual. First, do not interfere, shutdown, scan for viruses or anything. Any impact can lead to later processing and data recovery becoming more complicated and difficult. The best way to handle this is to backup all encrypted data to an independent storage system like HDD box, etc. Next, remove the hard drive, seal it and immediately consult an expert.
In HTI Services, we have years of experience in handling virus-encrypted data cases. Our experts will analyze the current state of the system, assess the potential risks encountered in the decoding process, thereby offering the most reasonable plan to ensure data for customers.



